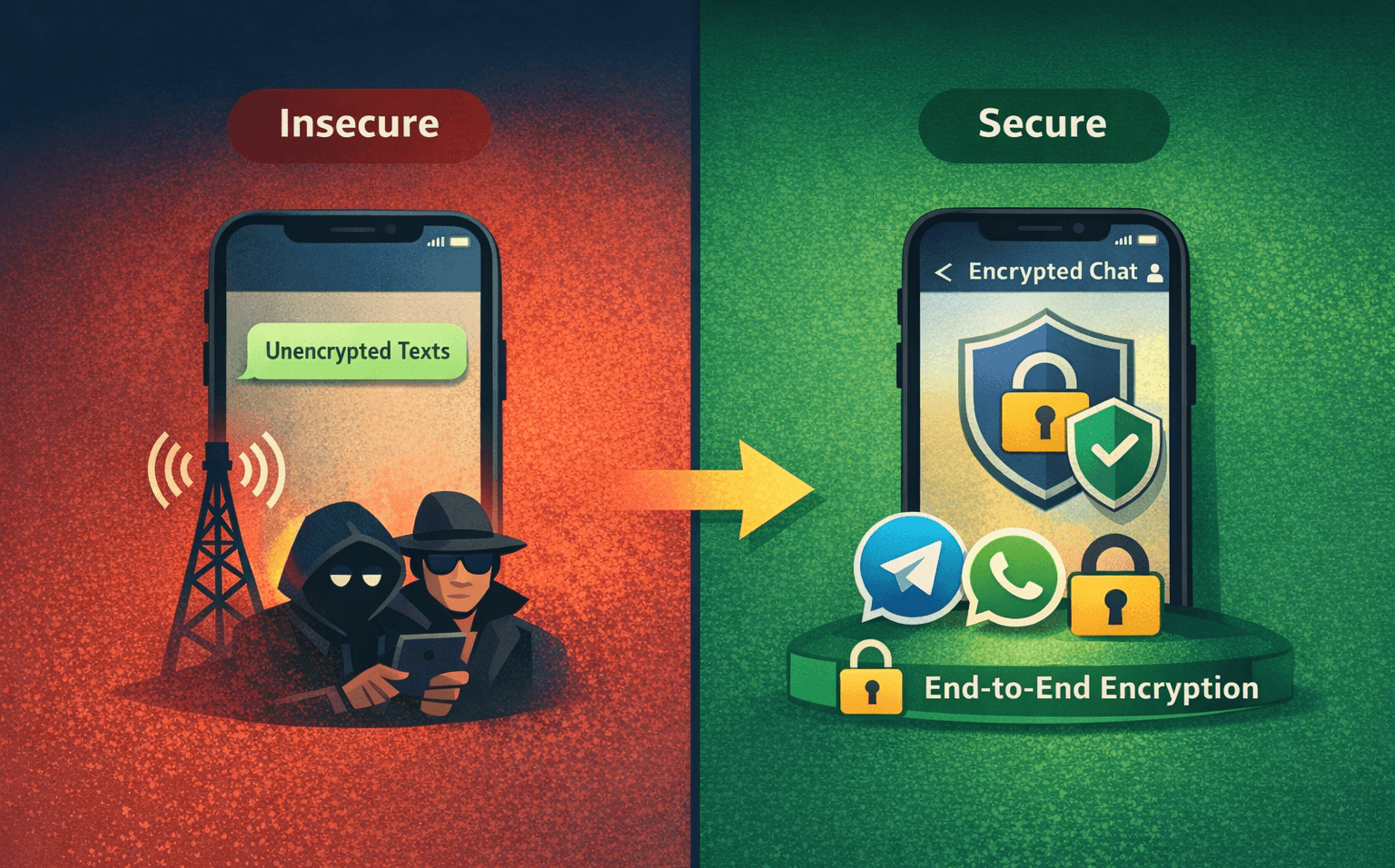
Federal cybersecurity officials have issued an unprecedented warning: stop using standard SMS and RCS text messages for sensitive conversations. Following revelations of extensive foreign surveillance operations targeting U.S. telecommunications infrastructure, agencies including CISA are urging Americans to adopt end-to-end encrypted messaging platforms immediately.
The advisory represents a significant shift in official guidance. For years, government agencies treated text messaging as reasonably secure for everyday communication. Recent breaches have shattered that assumption. Sophisticated threat actors have demonstrated the ability to intercept, read, and retain unencrypted messages at scale, exposing everything from personal conversations to business communications.
This article examines why traditional text messaging has become a security liability, what end-to-end encryption offers, and how to implement federal recommendations in your personal and professional communications.
Understanding the Encryption Gap in Modern Messaging
Traditional SMS and even newer RCS protocols transmit messages without meaningful encryption protection. This fundamental vulnerability has existed since the inception of cellular networks, but today's threat landscape makes it unacceptable for sensitive communications.
How Unencrypted Messages Expose Your Data
Standard text messages travel through multiple carrier systems before reaching their destination. At each point in this journey, the message exists in readable plaintext. Network operators, government agencies with legal access, and unauthorized attackers who breach telecom infrastructure can all intercept and read these communications.
The vulnerability extends beyond message content. Metadata including sender identity, recipient information, timestamps, and location data accompanies every text. This metadata creates detailed patterns of who communicates with whom, when, and from where—intelligence as valuable as message content itself.
Recent breaches have demonstrated that well-resourced adversaries maintain persistent access to major telecommunications networks. Once established, this access allows continuous surveillance of text message traffic without detection.
Why RCS Without Encryption Fails Security Standards
Rich Communication Services (RCS) was designed to modernize messaging with features like read receipts, typing indicators, and high-quality media sharing. However, most RCS implementations lack end-to-end encryption, leaving messages vulnerable to the same interception risks as SMS.
Google Messages offers RCS encryption between Android users, but this protection disappears when communicating with iPhone users or when carrier systems don't support encryption. The result is inconsistent security that users cannot reliably verify.
Table: SMS vs. RCS vs. Encrypted Messaging
| Feature | SMS | Standard RCS | End-to-End Encrypted Apps |
|---|---|---|---|
| Message encryption | None | Transport only | Full end-to-end |
| Metadata protection | None | Minimal | Significant |
| Cross-platform security | Consistent (none) | Inconsistent | Consistent (strong) |
| Carrier visibility | Complete | Complete | Minimal |
| Breach impact | Complete exposure | Complete exposure | Keys required |
The Persistent Device Storage Problem
Even when using encrypted messaging apps, federal guidance emphasizes another vulnerability: messages stored indefinitely on devices. If an attacker gains physical or remote access to your phone, stored message history becomes accessible regardless of transmission encryption.
This reality has prompted CISA to recommend enabling disappearing messages and regularly deleting sensitive conversations. Encryption protects messages in transit, but data-at-rest requires additional security layers including device encryption and access controls.
Federal Recommendations for Secure Messaging
CISA's advisory provides specific guidance for protecting sensitive communications. These recommendations apply to both personal and professional contexts where confidentiality matters.
Adopting End-to-End Encrypted Platforms
Federal agencies specifically recommend messaging applications that implement end-to-end encryption by default. Signal, WhatsApp, and Facebook Messenger all provide this protection, ensuring that only the sender and recipient can read message content.
End-to-end encryption means messages are encrypted on the sender's device and only decrypted on the recipient's device. Even if network traffic is intercepted or servers are breached, the encrypted messages remain unreadable without the recipient's private keys.
Key characteristics of acceptable encrypted messaging platforms:
- Encryption enabled by default for all conversations
- Open-source encryption protocols subject to independent security audits
- Minimal metadata collection and storage
- No backdoors or key escrow systems
- Cross-platform support for consistent security
Implementing Disappearing Messages
Beyond transit encryption, CISA recommends configuring messages to automatically delete after a specified period. This feature, available in Signal, WhatsApp, and Telegram, reduces the window of vulnerability if device security is compromised.
Disappearing messages address the reality that perfect device security is impossible to maintain. Lost phones, malware infections, and physical seizures can all expose message history. Automatic deletion limits this exposure to recent conversations rather than complete communication archives.
Important: Set disappearing message timers based on conversation sensitivity. Highly confidential discussions might warrant 24-hour or even shorter deletion windows, while routine coordination could use 7-day settings.
Regular Message History Cleanup
Even with disappearing messages enabled, users should manually review and delete sensitive conversations periodically. This practice ensures that configuration errors, app updates, or forgotten settings don't leave vulnerable data exposed.
Establish a routine schedule for message cleanup:
- Weekly: Review and delete sensitive business communications
- Monthly: Clear conversation history with financial advisors, healthcare providers, and legal contacts
- Quarterly: Archive important conversations to encrypted offline storage if retention is necessary, then delete from devices
The Apple RCS Encryption Development
Apple's testing of end-to-end encryption for RCS in iOS 18.3 beta represents progress toward secure cross-platform messaging, but current limitations prevent it from solving the security problem today.
Current Status and Carrier Support Gaps
The encryption feature exists in beta testing with only four French carriers (Bouygues Telecom, Orange, SFR, and Free Mobile) having the necessary infrastructure code. Even among these carriers, none have activated the encryption functionality for production users.
This limited deployment means the vast majority of iPhone users worldwide cannot access RCS encryption even in beta. U.S. carriers, which serve the largest iPhone user base, have not announced support timelines or implementation plans.
Why Partial Deployment Creates Security Risks
Inconsistent encryption support introduces a dangerous user experience problem: people cannot reliably determine whether their messages are protected. A conversation that starts with encryption might lose protection when participants travel internationally or switch carriers.
This uncertainty is precisely why federal agencies recommend dedicated encrypted messaging apps rather than waiting for carrier-dependent RCS encryption. Apps like Signal provide consistent, verifiable security regardless of carrier, device type, or user location.
Table: RCS Encryption Deployment Status
| Region | Carriers with Code | Active Deployment | User Access |
|---|---|---|---|
| France | 4 carriers | None yet | Beta testers only |
| United States | 0 carriers | None | Not available |
| Rest of World | Unknown | None | Not available |
| Timeline to General Availability | Unknown | Unknown | Months to years |
Additional Security Guidance from Federal Agencies
CISA's messaging security advice extends beyond encryption to address common attack vectors that compromise communications through social engineering and device vulnerabilities.
Avoiding Group Invitation Exploits
Federal guidance specifically warns against joining group chats via invitation links or QR codes from unknown sources. These mechanisms can deliver malware, enable account takeovers, or add users to harassment campaigns.
Verify group invitations through independent channels before accepting:
- Contact the supposed sender directly using a known phone number or email
- Confirm the legitimacy and purpose of the group
- Check the member list if visible before joining
- Decline invitations that create urgency or pressure immediate action
Recognizing Fake Security Alerts
Attackers increasingly impersonate platform security notifications to trick users into compromising their accounts. These fake alerts often claim suspicious activity, required verification, or impending account suspension.
Legitimate security alerts from messaging platforms follow consistent patterns. They appear within the app itself rather than through external text messages, never request passwords or verification codes, and provide account security pages accessible through official app menus rather than embedded links.
Pro Tip: Enable two-factor authentication on all messaging apps. When genuine security concerns arise, you can verify them through your registered 2FA device rather than responding to potentially fraudulent alerts.
Device Security as the Foundation
Messaging encryption becomes irrelevant if attackers compromise the device itself. Federal guidance assumes users implement fundamental device security:
- Strong device passwords or biometric authentication
- Automatic security updates enabled
- App installations restricted to official stores
- Phishing-resistant mindset for links and attachments
- Regular security audits of installed applications
Implementing Federal Recommendations in Practice
Transitioning from standard text messaging to encrypted platforms requires coordination with contacts and adjustment of communication habits. A systematic approach ensures security improvements don't create usability problems.
Selecting Your Primary Encrypted Platform
Choose a messaging app based on your contact network and security requirements. Signal offers the strongest privacy focus with minimal metadata collection. WhatsApp provides the largest user base and Meta's development resources. Facebook Messenger balances encryption with integration into the broader Facebook ecosystem.
For most users, adopting the platform where their most important contacts already have accounts minimizes friction. Advocate for additional contacts to join your chosen platform by explaining the security benefits without creating judgment around current practices.
Migrating Sensitive Communications
Identify which conversations contain sensitive information requiring encryption protection:
- Financial planning and investment discussions
- Healthcare information and medical consultations
- Legal matters and attorney communications
- Business strategy and competitive intelligence
- Personal information about family members
- Political or social activism coordination
Contact these conversation partners individually to suggest moving to encrypted messaging. Provide simple setup instructions and offer to help with the transition. Frame the change as protecting both parties rather than criticism of their current approach.
Maintaining Two-Tier Communication System
Practical reality means you'll maintain both encrypted apps for sensitive conversations and standard messaging for routine coordination. This dual system requires discipline to consistently route appropriate content through secure channels.
Table: Message Type Routing Decision Framework
| Content Type | Platform Choice | Rationale |
|---|---|---|
| Passwords, codes, PINs | Encrypted app, disappearing | Immediate deletion prevents exposure |
| Financial account details | Encrypted app | Persistent risk if compromised |
| Medical information | Encrypted app | HIPAA privacy obligations |
| Social coordination | Standard SMS acceptable | Low sensitivity, convenience priority |
| Travel plans | Encrypted app preferred | Security and location privacy |
Key Takeaways
- Federal agencies now explicitly warn against using unencrypted SMS and RCS for sensitive conversations due to confirmed telecommunications infrastructure breaches
- End-to-end encrypted messaging apps like Signal, WhatsApp, and Messenger provide the only reliable protection for message content in transit
- Enable disappearing messages and regularly delete sensitive conversations to limit exposure if device security is compromised
- Apple's RCS encryption testing represents future progress but remains unavailable to the vast majority of users and should not be relied upon today
- Implement device security fundamentals including strong authentication, automatic updates, and phishing awareness as the foundation for messaging security
- Avoid group invitation links from unknown sources and verify security alerts through official app channels rather than external messages
Conclusion
Federal cybersecurity agencies have fundamentally reassessed the security of standard text messaging. The combination of sophisticated threat actors, confirmed telecommunications breaches, and the availability of strong encryption alternatives has made unencrypted SMS and RCS unacceptable for sensitive communications.
Implementing these recommendations requires changing established communication habits and persuading contacts to adopt new platforms. The effort is justified by the genuine risks exposed through recent security incidents. As threat actors demonstrate increasing capabilities to access telecommunications infrastructure, the window for protecting sensitive conversations through encrypted messaging is closing.
Begin your transition today by selecting an encrypted messaging platform, enabling disappearing messages, and migrating your most sensitive conversations. The federal agencies issuing these warnings have access to classified intelligence about actual threats. Their guidance reflects real risks demanding immediate action.
Frequently Asked Questions
Q: Are all encrypted messaging apps equally secure?
A: No, significant differences exist in implementation quality, metadata protection, and corporate data access. Signal provides the strongest privacy guarantees with minimal metadata collection and no corporate access to message content. WhatsApp and Messenger offer strong encryption but collect more metadata and operate under Meta's corporate structure. All three substantially outperform unencrypted SMS and RCS for message content protection.
Q: Will using encrypted messaging apps make me a target for law enforcement scrutiny?
A: Federal agencies recommend encrypted messaging for ordinary citizens protecting sensitive personal information, not to shield criminal activity. Billions of people worldwide use these apps for legitimate privacy protection. Using encryption is normal security hygiene, similar to locking your doors or using passwords, and does not indicate wrongdoing.
Q: Can I trust that messaging apps truly implement end-to-end encryption?
A: Major platforms like Signal, WhatsApp, and Messenger use independently audited open-source encryption protocols. Security researchers continuously examine these implementations for vulnerabilities. While no system is perfect, these platforms have withstood extensive scrutiny and provide demonstrably stronger protection than unencrypted alternatives.
Q: What happens to my messages if I lose my phone?
A: End-to-end encryption means messages are tied to your device. Most platforms offer backup mechanisms with varying security properties. Signal provides encrypted backups you control. WhatsApp offers cloud backups through Apple iCloud or Google Drive. Without backups, losing your device means losing message history—which actually enhances security by limiting data exposure if the phone falls into wrong hands.
Q: How do I convince family members and colleagues to switch to encrypted messaging?
A: Focus on practical benefits rather than abstract threats. Explain that major apps are free, easy to use, and protect private information from corporate surveillance and data breaches. Offer to help with installation and initial setup. For elderly relatives, emphasize protection against scams. For colleagues, highlight compliance with security best practices and protection of business information. Lead by example rather than judgment.
