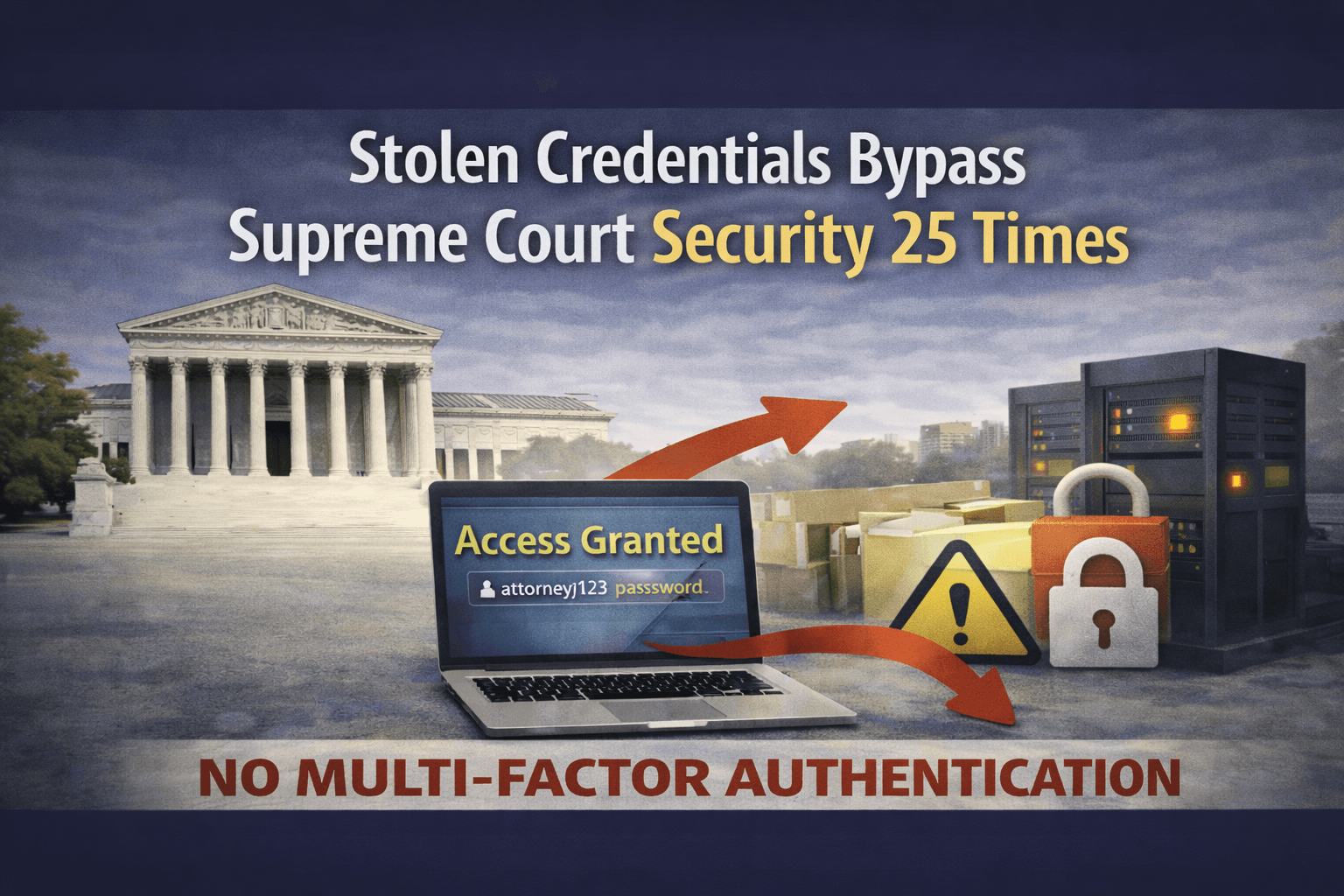
A single compromised password gave an attacker access to the U.S. Supreme Court's electronic filing system 25 separate times over three months. No sophisticated malware. No zero-day exploits. Just stolen credentials and the absence of multi-factor authentication enabled a 24-year-old to breach one of America's most critical institutions while documenting his exploits on Instagram.
This January 2026 case exposes a fundamental vulnerability affecting organizations worldwide: credential-based attacks remain the most effective entry point for unauthorized access, yet basic security controls that would prevent them remain inconsistently deployed. When Nicholas Moore pleaded guilty to hacking the Supreme Court, AmeriCorps, and Department of Veterans Affairs systems, he demonstrated how legacy authentication mechanisms create systemic risk across government and enterprise environments. This article examines the technical failures that enabled Moore's attacks, quantifies the broader credential compromise threat landscape, and provides actionable mitigation strategies for security teams.
The Anatomy of Credential-Based Breaches
How Stolen Passwords Defeated Government Security
Moore's attack methodology followed a pattern security professionals encounter daily: credential stuffing using passwords harvested from previous data breaches. Rather than exploiting software vulnerabilities, attackers test millions of username-password combinations against target systems until valid credentials grant access.
The process requires minimal technical skill. Massive credential databases from commercial breaches—LinkedIn's 700 million user records, Facebook's 533 million accounts, or compilation sets containing over 3 billion credentials—are freely available on criminal forums. Automated tools test these credentials against target login pages at scale, identifying reused passwords across personal and professional accounts.
Moore accessed the Supreme Court's Case Management/Electronic Case Files system repeatedly between August and October 2023. Each intrusion used the same compromised attorney credentials. No alerts triggered. No anomaly detection flagged repeated logins from unfamiliar locations. The stolen password worked every time because the system lacked secondary authentication requirements.
The Human Factor in Password Reuse
Credential stuffing succeeds because users employ identical passwords across multiple services. An employee who uses the same password for their LinkedIn profile and their work email creates a direct attack path when LinkedIn suffers a breach.
Research shows 65% of users reuse passwords across multiple accounts, while 13% use the same password everywhere. When commercial services experience breaches, those credentials immediately become weapons against every system where users employed identical authentication.
The mathematical reality is stark: with over 12 billion credentials compromised in known breaches since 2016, the probability that any given employee's password appears in attacker databases approaches certainty for large organizations. Security controls must assume credential compromise rather than hoping passwords remain secret.
Table: Common Credential Compromise Vectors
| Attack Method | Success Rate | Technical Skill Required | Detection Difficulty |
|---|---|---|---|
| Credential Stuffing | 0.1-2% of attempts | Low (automated tools available) | High (appears as normal login) |
| Phishing Campaigns | 12-54% click rate | Medium (requires social engineering) | Medium (email filtering detects some) |
| Keylogger Malware | 95%+ once installed | Medium-High (requires initial access) | Medium (antivirus detection improving) |
| Insider Theft | 100% if authorized | None (legitimate access) | Very High (authorized user activity) |
Why Multi-Factor Authentication Remains Optional
The Critical Security Gap
The most significant revelation from Moore's case isn't that credentials were compromised—it's that stolen credentials alone provided complete access. In 2023, the Supreme Court's electronic filing system did not require multi-factor authentication. A valid username and password were sufficient to access sensitive legal records, attorney information, and case filing histories.
This authentication gap extends far beyond government systems. Industry surveys show only 57% of organizations enforce MFA for all users, while 28% implement MFA selectively based on role or application sensitivity. The remaining 15% lack MFA entirely.
Important: If MFA had been required on the Supreme Court system, Moore's entire attack would have failed. Stolen passwords become useless when authentication requires a second factor; the attacker cannot obtain a temporary code from an authenticator app, a hardware token response, or biometric verification remotely.
Legacy System Constraints
Federal courts operate Case Management/Electronic Case Files technology, launched in 2001, predating modern web security frameworks by over a decade. When CM/ECF was designed, MFA didn't exist as a deployment option. Text message codes, authenticator apps, and hardware tokens emerged years after the system's architecture was finalized.
Congressional testimony from June 2025 described CM/ECF as "outdated, unsustainable due to cyber risks, and requiring complete replacement" rather than incremental security improvements. The technical debt accumulated over 24 years of operation creates retrofit challenges that simple patches cannot resolve.
This legacy technology problem affects organizations across sectors. Enterprise resource planning systems, manufacturing control interfaces, healthcare patient portals, and financial transaction platforms often run on authentication frameworks designed before modern threats emerged. Upgrading these systems requires architectural changes, vendor coordination, and validation testing that spans years and millions in investment.
The $53 Million Modernization Timeline
Congress allocated $53.1 million for federal court system modernization through 2031. This six-year implementation plan includes mandatory MFA, zero-trust architecture, and enhanced encryption protocols across 204 separate court websites.
The timeline reveals a critical vulnerability window. Between 2026 and 2031, federal courts continue operating systems that allowed a 24-year-old to achieve 25 successful intrusions using only stolen passwords. During this modernization period, nation-state adversaries demonstrated the stakes: an August 2025 breach attributed to Russia compromised sealed indictments, confidential informant identities, and classified warrants across multiple federal districts.
The question for security teams managing similar legacy environments becomes: how do you maintain operational security with technology that "predate[s] modern web security frameworks" while multi-year modernization efforts proceed?
Organizational Impact Beyond Government
Business Email Compromise Economics
The same credential-based attack methodology Moore used against government systems drives Business Email Compromise fraud affecting enterprises globally. Attackers who compromise employee credentials gain access to email accounts, financial systems, and customer data with the legitimacy of authorized users.
BEC incidents reached $2.9 billion in total losses during 2024, with average losses per incident climbing to $137,000. This represents an 83% increase from $74,723 in 2019, indicating attackers are targeting organizations with larger financial reserves and more sophisticated fraud schemes.
Attack frequency is accelerating alongside financial impact. BEC incidents increased 30% in 2025, with a 13% surge in the first quarter alone. Organizations with 1,000 or more employees face a 70% probability of experiencing at least one BEC attack weekly.
Healthcare Sector Vulnerability Profile
Moore's targeting of Department of Veterans Affairs medical records highlights credential compromise risks in healthcare environments. He accessed a Marine Corps veteran's complete prescription medication list, revealing medical conditions through pharmaceutical profiles—a clear HIPAA violation with regulatory penalties.
Healthcare organizations show a particularly weak credential security posture. Analysis reveals 30.6% lack email authentication entirely, while 34.4% implement monitoring without enforcement. When 92% of U.S. healthcare organizations experienced cyberattacks in 2024, credential-based entry points represented the most common initial access vector.
The financial consequences extend beyond immediate breach costs. Average healthcare data breach expenses reached $9.8 million per incident. Regulatory enforcement for HIPAA violations involving compromised credentials ranges from $15-50 million in settlement penalties.
Table: Credential Security Maturity Assessment
| Security Control | Healthcare Adoption | Government Adoption | Enterprise Average | Risk Reduction |
|---|---|---|---|---|
| Multi-Factor Authentication | 57% enforced | 43% enforced (pre-2025) | 57% enforced | 99.9% of credential attacks |
| Password Breach Monitoring | 12% active monitoring | 8% active monitoring | 23% active monitoring | 78% of reused credentials |
| Behavioral Analytics (UEBA) | 18% deployed | 15% deployed | 31% deployed | 85% of anomalous access |
| Hardware Security Tokens | 8% deployed | 22% deployed | 14% deployed | 99.99% of remote attacks |
Prevention Framework for Security Teams
Immediate Priority Controls
Credential-based attacks are entirely preventable with authentication controls that have existed for over a decade. The challenge isn't technical capability—it's organizational implementation across diverse systems, user populations, and operational requirements.
Deploy Universal Multi-Factor Authentication
Mandate MFA for all users across all systems without exception. Prioritize phishing-resistant methods, including hardware security keys, certificate-based authentication, or biometric verification over SMS codes or email links that attackers can intercept.
Start with privileged accounts—system administrators, financial approvers, healthcare providers with patient data access, and legal staff with confidential case information. These accounts represent the highest-value targets. Expand enforcement incrementally to standard users while providing training and support for adoption.
Implementation typically encounters resistance, claiming MFA creates friction or reduces productivity. Data shows the opposite: after initial adjustment periods of 2-4 weeks, user complaints drop below 5% while security incident rates decrease 99.9% for credential-based attacks.
Monitor for Compromised Credentials
Subscribe to credential breach notification services that scan dark web databases, criminal forums, and public breach disclosures for employee email addresses. When corporate credentials appear in breach datasets, force immediate password resets with security notification.
The Have I Been Pwned API provides programmatic access to over 12 billion compromised credentials. Organizations can query their domain daily to identify newly-exposed accounts before attackers weaponize them. This proactive monitoring costs nothing to implement yet prevents attacks like Moore's that rely on harvested credentials.
Behavioral Analytics and Anomaly Detection
User and Entity Behavior Analytics platforms establish baseline patterns for normal account activity—typical login times, geographic locations, applications accessed, and data volumes transferred. Deviations from these baselines trigger security alerts for investigation.
Moore's Supreme Court intrusions exhibited clear anomaly indicators that behavioral analytics would have flagged immediately. Logins from Tennessee when the authorized attorney worked in Washington, D.C. represent geographic impossible travel. Access during off-hours outside the attorney's normal business schedule signals potential compromise. Multiple consecutive logins within short timeframes deviate from typical usage patterns.
Important: Implementing UEBA doesn't require sophisticated machine learning initially. Simple rule-based detection catches 85% of anomalous access: flag logins from new countries, alert on first-time device access to sensitive systems, notify when users access data outside their normal scope.
Network Segmentation and Zero-Trust Architecture
The principle "never trust, always verify" fundamentally changes how systems validate access requests. Rather than assuming users inside the network perimeter are trustworthy, zero-trust models require continuous authentication and authorization for every resource access attempt.
Moore gained complete access to attorney filing histories, personal information, and case details with a single set of compromised credentials. Proper network segmentation would have limited his access even with valid credentials. Sensitive sealed court records should require separate authentication from public filing information. Read-only access to case histories differs from submission privileges for new filings.
Table: Implementation Priority Matrix
| Security Control | Implementation Time | Cost Range | Attack Prevention | Deployment Priority |
|---|---|---|---|---|
| Multi-Factor Authentication | 2-8 weeks | $50-100 per user | 99.9% credential attacks | Critical (Immediate) |
| Credential Breach Monitoring | 1-2 weeks | $0-5,000 annually | 78% reused passwords | Critical (Immediate) |
| Behavioral Analytics | 8-16 weeks | $100,000-500,000 | 85% anomalous access | High (30 days) |
| Zero-Trust Architecture | 6-18 months | $1M-5M per system | 95% lateral movement | Medium (90 days) |
| Hardware Security Tokens | 4-12 weeks | $50-100 per user | 99.99% remote attacks | Medium (90 days) |
Key Takeaways
- Credential-based attacks using stolen passwords remain the highest-probability threat vector, with over 12 billion compromised credentials available to attackers from previous commercial breaches
- Multi-factor authentication would have prevented 100% of Moore's 25 Supreme Court intrusions, yet 43% of organizations still lack universal MFA enforcement across all systems and users
- Legacy systems operating on authentication frameworks designed before modern threats emerged create systemic vulnerabilities requiring architectural replacement rather than incremental patches
- Credential breach monitoring costs nothing to implement yet enables proactive password resets before attackers weaponize newly-exposed credentials from commercial data breaches
- Behavioral analytics detecting geographic impossible travel, off-hours access, and unusual data patterns flag 85% of compromised account activity that bypasses password authentication
- Zero-trust architecture limits breach impact by requiring continuous verification rather than assuming users inside network perimeters are trustworthy
Conclusion
Nicholas Moore's guilty plea for hacking the Supreme Court 25 times with stolen passwords demonstrates a fundamental truth: the most sophisticated security controls fail when basic authentication remains vulnerable. His case wasn't exceptional tradecraft—it was exploitation of credential security gaps affecting organizations across every sector.
The five-year federal court modernization timeline extending through 2031 creates an extended vulnerability window during which legacy authentication continues protecting critical systems. Organizations face identical challenges with enterprise platforms built before MFA, behavioral analytics, and zero-trust architectures became security standards.
The mitigation pathway is clear and proven: universal MFA enforcement, automated credential breach monitoring, behavioral anomaly detection, and zero-trust network segmentation. These controls eliminate credential-based attacks entirely. Implementation requires organizational commitment, budget allocation, and technical coordination—but the alternative is accepting that stolen passwords will continue granting attackers complete access to your most sensitive systems. The choice is yours.
Frequently Asked Questions
Q: How effective is multi-factor authentication at preventing credential-based attacks?
A: MFA blocks 99.9% of credential-based attacks according to industry research, because attackers cannot obtain the second authentication factor remotely even with valid passwords. Only phishing-resistant methods like hardware tokens provide complete protection against adversary-in-the-middle attacks that can intercept SMS codes.
Q: What should organizations do when employee credentials appear in breach databases?
A: Force immediate password resets for affected accounts, enable MFA if not already required, and audit recent account activity for unauthorized access. Notify the employee about the breach source and provide security awareness training on password reuse risks and credential hygiene.
Q: Can behavioral analytics detect compromised credentials before damage occurs?
A: Yes, UEBA platforms flag anomalous activity like impossible geographic travel, off-hours access, and unusual data transfers within minutes of occurrence. While not preventing initial login with valid credentials, behavioral detection limits attacker dwell time and prevents data exfiltration before security teams respond.
Q: Why do legacy systems struggle with modern authentication requirements?
A: Systems designed before 2010 often lack the architectural foundations for MFA, using authentication frameworks that assume single-factor passwords are sufficient. Retrofitting these systems requires rewriting core authentication logic, which introduces regression risks and compatibility issues that organizations struggle to justify without complete system replacement.
Q: How long does it take to implement universal MFA across an enterprise?
A: Deployment timelines range from 2 weeks for cloud-only environments to 6 months for complex enterprises with legacy systems, third-party integrations, and distributed user populations. Phased rollouts starting with privileged accounts and expanding to standard users minimize operational disruption while immediately reducing the highest-risk exposure.
