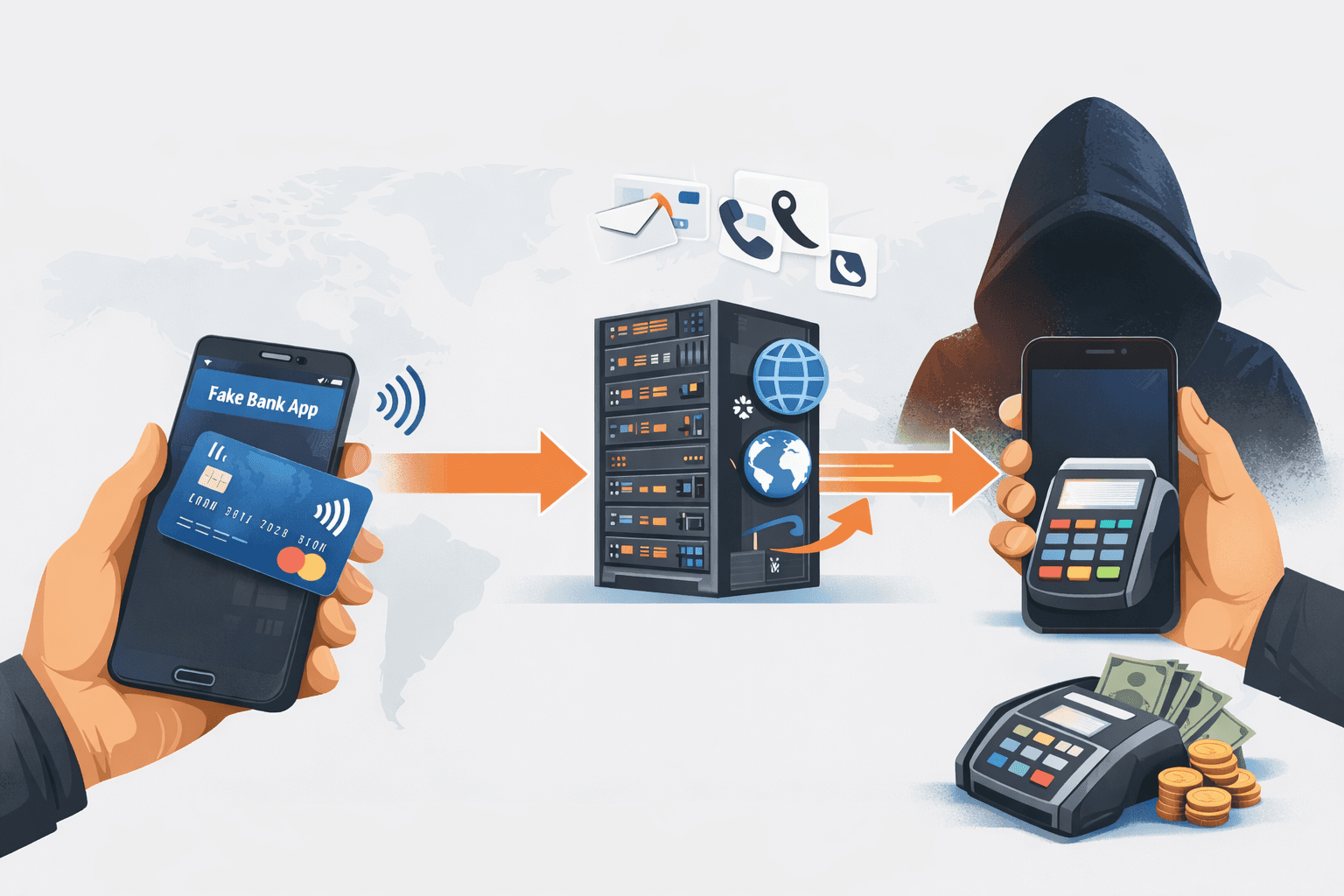
Between August 2024 and August 2025, cybersecurity researchers documented over 54 variants of a sophisticated fraud scheme that transforms ordinary Android phones into remote payment relays. Ghost Tapped attacks trick victims into installing malicious banking apps that capture contactless payment card data through NFC technology, then relay this information to attackers who execute unauthorized transactions at physical point-of-sale terminals worldwide.
This emerging threat represents a dangerous evolution in payment fraud. Unlike traditional card skimming that requires physical card readers, Ghost Tapped operations use social engineering to convince victims to voluntarily tap their cards against their own phones. One criminal operation alone processed at least $355,000 in fraudulent transactions over ten months, with victims spanning multiple continents and law enforcement making arrests in the United States, Singapore, Czech Republic, and Malaysia.
The technical sophistication and global reach of Ghost Tapped campaigns signal a critical vulnerability in mobile payment security. Organizations and individuals using contactless payment methods must understand how these attacks work, recognize the warning signs, and implement defensive measures before becoming the next victims.
Understanding the Ghost Tapped Attack Chain
Ghost Tapped operations follow a multi-stage attack pattern that exploits both technical vulnerabilities and human psychology. The scheme combines social engineering, malicious mobile applications, and real-time data relay infrastructure to conduct fraud at scale.
Initial Compromise Through Social Engineering
Attackers initiate contact with potential victims through phishing messages and voice calls that impersonate legitimate financial institutions. These communications create urgency around security concerns, account verification needs, or mandatory app updates that require immediate action.
The social engineering tactics typically include:
- SMS messages claiming suspicious account activity requiring verification
- Phone calls from spoofed numbers matching official bank customer service lines
- Emails with urgent security alerts directing users to download "updated" banking apps
- Fake customer support representatives providing step-by-step installation guidance
- Threats of account suspension or closure if immediate action isn't taken
Victims are directed to download Android Package (APK) files from third-party sources rather than official app stores. The attackers often walk victims through disabling security settings that normally prevent sideloading applications, making the installation process seem like a routine security measure.
Malicious App Installation and Permissions
Once installed, Ghost Tapped applications request permissions that enable the fraud scheme to function. The apps masquerade as legitimate banking or payment applications with convincing user interfaces that replicate official designs.
Critical permissions requested include:
- NFC reading capabilities to capture contactless card data
- Internet connectivity for real-time data transmission
- Device identification access to track infected phones
- Notification access to monitor authentication messages
- Overlay permissions to display fake interfaces over legitimate apps
The registration process instructs victims to tap their physical payment cards against their phone's NFC reader, supposedly to verify identity or activate enhanced security features. During this interaction, the malicious app captures all data transmitted through the card's NFC chip.
Data Capture and Command-and-Control Communication
When victims tap their cards, the Ghost Tapped app's reader component extracts payment credential data transmitted via NFC. This information includes card numbers, expiration dates, and authentication tokens used for contactless transactions.
Table: Data Harvested by Ghost Tapped Applications
| Data Type | Purpose | Risk Level |
|---|---|---|
| NFC payment credentials | Card emulation for fraudulent transactions | Critical |
| Device identifiers (IMEI, Android ID) | Tracking infected devices | High |
| Authentication tokens | Bypassing transaction verification | Critical |
| Network information | Optimizing relay connections | Medium |
| Installed app lists | Identifying additional attack vectors | Medium |
The captured data is encrypted and transmitted to attacker-controlled command-and-control servers using protocols designed for real-time communication. Group-IB research identified WebSocket and MQTT protocols as primary channels, chosen for their ability to maintain persistent connections with low latency.
These C2 servers coordinate the relay between infected victim devices and attacker-operated tapper applications. The infrastructure supports simultaneous connections from multiple compromised phones, enabling scalable fraud operations.
Real-Time Transaction Relay and Execution
On the attacker side, specialized tapper applications running on separate Android devices receive the relayed payment data. These devices are physically positioned at point-of-sale terminals or ATMs, often equipment that has been stolen or fraudulently obtained.
The tapper app uses Host Card Emulation (HCE) technology to emulate the victim's payment card. When the attacker device is brought near a payment terminal, the terminal detects what appears to be a legitimate contactless card physically present at the transaction location.
From the payment terminal's perspective, these transactions are indistinguishable from normal contactless payments. The card data, authentication tokens, and transaction protocols all match what would occur if the actual physical card were being used. Payment networks authorize the transactions accordingly.
Important: Once a card has been tapped on an infected device, attackers can execute transactions repeatedly without requiring additional access to the physical card or victim interaction. The compromised phone continues relaying payment capabilities as long as the malicious app remains installed and active.
Technical Infrastructure Behind Ghost Tapped Operations
The Ghost Tapped ecosystem relies on sophisticated technical infrastructure that enables real-time fraud at global scale. Understanding these components reveals both the capabilities of modern cybercriminals and potential intervention points for defense.
Malware Variants and Distribution Networks
Group-IB identified at least 54 distinct Ghost Tapped application variants active between August 2024 and August 2025. These variants share core functionality while incorporating different obfuscation techniques, user interfaces, and targeting profiles.
Major malware families marketed on Telegram include:
- TX-NFC: Feature-complete toolkits with custom C2 panels
- Related kits sold as "turnkey" fraud solutions
- White-label versions customized for specific geographic markets
- Modular variants allowing operators to select capabilities
The underground economy surrounding these tools includes technical support, updates addressing security patches, and forums where operators share operational tactics. Pricing models range from one-time purchases to subscription services with ongoing support.
Distribution occurs primarily through Telegram channels, darknet marketplaces, and direct messaging to potential operators. Some variants are packaged with documentation explaining social engineering scripts and optimal targeting strategies.
NFC Technology Exploitation
Ghost Tapped attacks exploit legitimate NFC functionality built into Android devices and contactless payment cards. Near Field Communication enables data exchange over distances of approximately 4 centimeters, designed for convenient contactless payments.
Modern payment cards store credential data in secure elements that respond to NFC reader requests. During normal transactions, this data enables payment terminals to verify card authenticity and authorize charges without requiring physical card insertion or magnetic stripe reading.
Table: NFC Exploitation in Ghost Tapped vs. Legitimate Use
| Aspect | Legitimate Use | Ghost Tapped Exploitation |
|---|---|---|
| Data access | Authorized payment terminals only | Malicious apps capture credentials |
| Transaction location | Physical card at POS | Remote emulation via relay |
| User consent | Intentional payment action | Unknowing data harvesting |
| Frequency | Per-transaction card presence | Unlimited transactions post-compromise |
Android's Host Card Emulation (HCE) allows applications to emulate contactless cards, originally intended for digital wallet implementations. Ghost Tapped tapper apps abuse this capability to present stolen credentials as if they were legitimate card emulations.
The relay attack succeeds because payment networks cannot distinguish between a physical card at a terminal and an HCE-emulated card presenting identical credential data. Current contactless payment protocols lack strong transaction binding to specific device locations.
Command-and-Control Architecture
The C2 infrastructure supporting Ghost Tapped operations requires high reliability and low latency to enable real-time transaction relay. Attackers deploy servers in multiple geographic locations to optimize connection speeds and provide redundancy.
WebSocket and MQTT protocols serve as primary communication channels. WebSocket provides full-duplex communication over persistent TCP connections, ideal for bidirectional data flow between infected devices and tapper apps. MQTT offers lightweight publish-subscribe messaging suitable for mobile networks with variable connectivity.
Pro Tip: Network security teams should monitor for unusual WebSocket and MQTT traffic from mobile devices, particularly persistent connections to suspicious IP addresses or domains. Anomalous outbound traffic patterns from employee devices may indicate compromise.
The C2 infrastructure typically includes:
- Load-balanced server clusters handling multiple simultaneous relay sessions
- Database systems storing harvested credentials and device inventories
- Administrative panels allowing operators to manage compromised devices
- Encryption layers protecting attacker communications from interception
- Geographically distributed nodes reducing detection risk
Some operations employ bulletproof hosting services that resist takedown efforts, while others use compromised legitimate servers to blend malicious traffic with normal activity.
Identifying and Preventing Ghost Tapped Infections
Defending against Ghost Tapped attacks requires both technical controls and user awareness. Organizations must implement layered security measures while educating personnel about social engineering tactics.
Recognition Warning Signs
Several indicators can help identify potential Ghost Tapped attacks before compromise occurs. Users should immediately become suspicious when encountering these red flags:
- Unsolicited communications requesting app installation outside official stores
- Instructions to disable Android security settings or allow unknown sources
- Requests to tap physical payment cards for "registration" or "verification"
- Pressure tactics creating urgency around account security issues
- Customer service representatives providing APK download links
Important: Legitimate financial institutions never ask customers to download apps from unofficial sources or disable device security features. Any such request indicates a social engineering attempt.
After installation, Ghost Tapped apps exhibit behavioral patterns that may reveal their malicious nature:
- Persistent requests for NFC and internet permissions
- Unusual battery drain from continuous background activity
- Network activity when the app should be idle
- Requests for permissions unrelated to stated functionality
- User interfaces with subtle differences from legitimate apps
Organizations should implement mobile threat detection solutions that monitor installed applications, permission usage, and network communications for suspicious patterns.
Technical Security Controls
Android security features provide important protections when properly configured. Organizations managing corporate devices should enforce these baseline controls:
Table: Essential Android Security Configurations
| Control | Configuration | Protection Provided |
|---|---|---|
| App sources | Play Protect enabled, unknown sources blocked | Prevents sideloading malicious APKs |
| Permission management | Review app permissions regularly | Limits malware capabilities |
| OS updates | Automatic security patches enabled | Addresses known vulnerabilities |
| Mobile Device Management | Centralized policy enforcement | Ensures consistent security posture |
| Network security | VPN usage, DNS filtering | Detects and blocks C2 communications |
Google Play Protect scans apps for malicious behavior, though determined attackers may evade detection through obfuscation techniques. Regular manual permission reviews help identify apps requesting unnecessary access.
Organizations should implement mobile device management (MDM) solutions that enforce security policies, detect jailbroken or rooted devices, and monitor for suspicious applications. MDM platforms can block installation of apps from untrusted sources and enforce encryption requirements.
User Education and Awareness Programs
Technical controls provide necessary but insufficient protection. Comprehensive security awareness training must address social engineering tactics specific to mobile fraud schemes.
Effective training programs should cover:
- Recognition of phishing messages and voice phishing (vishing) calls
- Verification procedures for unsolicited banking communications
- Understanding official app installation procedures through authorized stores
- Risks associated with sideloading applications or disabling security settings
- Proper responses when receiving suspicious communications
Training should emphasize that users should independently contact financial institutions using official contact information rather than responding to unsolicited messages. Phone numbers, email addresses, and web links provided by potential attackers should never be trusted.
Organizations should conduct simulated phishing exercises specifically targeting mobile devices to assess user readiness and identify personnel requiring additional training. These exercises reveal gaps in security awareness before real attacks succeed.
Incident Response Procedures
Despite preventive measures, some infections will occur. Organizations need clear procedures for responding to suspected Ghost Tapped compromises:
- Immediately power off the suspected device to halt any active relay sessions
- Contact the financial institution to freeze affected cards and dispute fraudulent charges
- Isolate the device from corporate networks to prevent lateral movement
- Capture forensic evidence including installed apps, permissions, and network logs
- Factory reset the device after evidence preservation
- Review transaction histories across all accounts for unauthorized activity
- Update passwords and authentication credentials on clean devices
Financial institutions typically have fraud protection policies covering unauthorized transactions, though reporting requirements and timeframes vary. Prompt reporting maximizes recovery prospects.
Organizations should maintain incident response playbooks specifically addressing mobile device compromises, including contact lists for financial institutions, law enforcement, and cybersecurity incident response teams.
The Broader Context of NFC Relay Fraud
Ghost Tapped represents one campaign within a larger trend of attackers exploiting NFC technology for financial fraud. Understanding this broader context reveals the scope of the threat and likely future developments.
Historical Evolution of NFC-Based Attacks
NFC relay attacks targeting payment systems have evolved significantly over the past decade. Early attacks focused on relay-only schemes requiring physical proximity to both the victim's card and payment terminal simultaneously.
Previous campaigns documented by security researchers involved more than 700-760 malicious Android applications conducting similar NFC relay fraud against banks and payment platforms worldwide. These operations demonstrated the viability of NFC exploitation at scale.
Ghost Tapped advances this attack model by eliminating the need for physical proximity to the victim during transactions. Once initial compromise occurs, attackers can execute transactions from anywhere with internet connectivity, dramatically expanding operational flexibility.
The industrialization of these attacks through malware-as-a-service models has lowered barriers to entry. Criminal operators without technical expertise can purchase ready-made toolkits and begin fraud operations within days.
Global Impact and Law Enforcement Response
The international nature of Ghost Tapped operations complicates law enforcement efforts. Victims may be located in one country while attackers operate from another and execute transactions in a third jurisdiction.
Documented arrests in the United States, Singapore, Czech Republic, and Malaysia demonstrate coordinated international law enforcement action. However, the decentralized nature of these operations means disrupting individual cells has limited impact on overall campaign activity.
Financial losses extend beyond direct fraudulent transactions. Banks face chargebacks, investigation costs, and reputational damage. Victims experience financial stress, time spent resolving fraud issues, and potential impacts to credit ratings if unauthorized charges aren't promptly resolved.
The estimated $355,000 processed by a single operation represents only detected and reported fraud. The true financial impact likely exceeds this figure substantially when accounting for unreported incidents and operations not yet discovered by researchers.
Future Threat Trajectory
Several factors suggest Ghost Tapped-style attacks will continue evolving:
- Increasing smartphone penetration globally expands the potential victim pool
- Growing adoption of contactless payments creates more targets
- Underground markets continue refining malware capabilities
- Social engineering tactics adapt to security awareness efforts
- Geographic expansion into markets with less mature mobile security
Defenders should anticipate variants incorporating additional capabilities such as:
- Enhanced evasion techniques targeting mobile security solutions
- Integration with other fraud schemes like account takeover attacks
- Exploitation of emerging payment technologies beyond NFC
- Improved social engineering using AI-generated voice and video
- Targeting of organizational payment systems and corporate cards
The fundamental vulnerabilities enabling Ghost Tapped attacks—lack of strong device location binding in contactless payment protocols and social engineering susceptibility—will require systemic changes in payment infrastructure and security awareness to address comprehensively.
Key Takeaways
- Ghost Tapped attacks transform victims' Android phones into permanent payment relays through malicious apps disguised as legitimate banking applications
- Over 54 malware variants have been identified, with criminal toolkits sold on Telegram enabling fraud operations that process hundreds of thousands of dollars
- Once a payment card is tapped on an infected device, attackers can repeatedly execute unauthorized transactions without further victim interaction
- Technical defenses must combine application source restrictions, permission management, and network monitoring with comprehensive user awareness training
- Organizations should implement incident response procedures specifically addressing mobile device compromises and maintain relationships with financial institutions for rapid fraud reporting
- The broader trend of NFC relay fraud involves over 700 malicious Android apps targeting payment systems globally, indicating systematic exploitation rather than isolated incidents
Conclusion
Ghost Tapped represents a sophisticated convergence of social engineering and technical exploitation that transforms mobile devices into instruments of financial fraud. The scheme's success depends on convincing victims to bypass Android security protections and voluntarily provide payment credentials through what appears to be routine security verification.
The documented global reach, substantial financial losses, and rapid evolution of these attacks demand immediate organizational attention. No sector is immune—Ghost Tapped operations target individuals, small businesses, and enterprise users indiscriminately.
Effective defense requires layered security combining technical controls, policy enforcement, and security awareness education. Organizations must treat mobile devices as critical components of their attack surface requiring the same security rigor applied to traditional endpoints. Begin by auditing current mobile security policies, implementing MDM solutions if not already deployed, and scheduling comprehensive security awareness training that specifically addresses mobile fraud tactics.
Frequently Asked Questions
Q: Can iPhones be infected with Ghost Tapped malware?
A: Current Ghost Tapped campaigns specifically target Android devices due to the platform's ability to sideload applications and more permissive NFC access. Apple's iOS restrictions on NFC usage and app installation make similar attacks significantly more difficult. However, users of all platforms should remain vigilant about phishing attempts and only install apps from official stores.
Q: How can I tell if my Android phone is already infected with Ghost Tapped malware?
A: Check your installed apps for unfamiliar banking or payment applications, review app permissions for suspicious NFC or internet access, and monitor for unusual battery drain or network activity. If you recently tapped a payment card on your phone following unsolicited instructions, immediately contact your financial institution and consider factory resetting your device after backing up essential data.
Q: Are contactless payment cards inherently insecure due to this vulnerability?
A: Contactless cards remain generally secure for normal use at legitimate payment terminals. Ghost Tapped exploits user trust rather than card technology weaknesses, tricking victims into providing credentials to malicious applications. The underlying issue is the inability of payment networks to verify that a card is physically present at the terminal rather than being emulated through relay.
Q: What should I do if I receive a call from someone claiming to be from my bank and requesting app installation?
A: Hang up immediately and independently contact your bank using the phone number on your physical card or official bank statement. Legitimate financial institutions never call customers requesting app installation from unofficial sources or asking them to tap cards for registration. Any such request indicates a social engineering attempt.
Q: Can antivirus software on my phone detect and remove Ghost Tapped malware?
A: Quality mobile security solutions can detect many Ghost Tapped variants, though determined attackers continually develop evasion techniques. Install security software from reputable vendors through official app stores, keep it updated, and combine it with other protective measures like disabling app installation from unknown sources and maintaining security awareness about social engineering tactics.
